How did I gain RCE and dump the database from the exploit desktop application?
Hi Hackers My name is Ahmed Mosaa, Senior Cyber Security Engineer, and this engagement has been done at one of the biggest financial institutions in my country. In this article, I will explain how I got full DB access and then got RCE on the DB server. So give me your concentration, and let’s start.

It was a normal thick client application (desktop) penetration test engagement, and I used my methodology for this kind of pentesting.
So at first, I tried to reverse the application, and luckily the application is written in C#, so it was easy to get the source code of the application using the dnSpy tool. and this is a small snippet of code.

Then, after a deep analysis of the source code, I found the application uses the database to make users login or perform other actions.
Okay, how does the application authenticate to the database?
To answer this question, I should have analyzed the code more until I found the application was calling file in the installation path contained configurations, and between those configurations, I found the DB credentials, as shown in the image below.
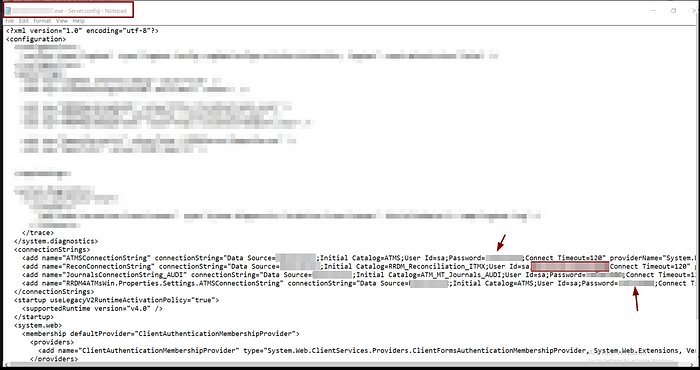
Nice now let try this credentials to open the DB using Microsoft sql server management studio

Awesome, we logged in to the to the DB server.
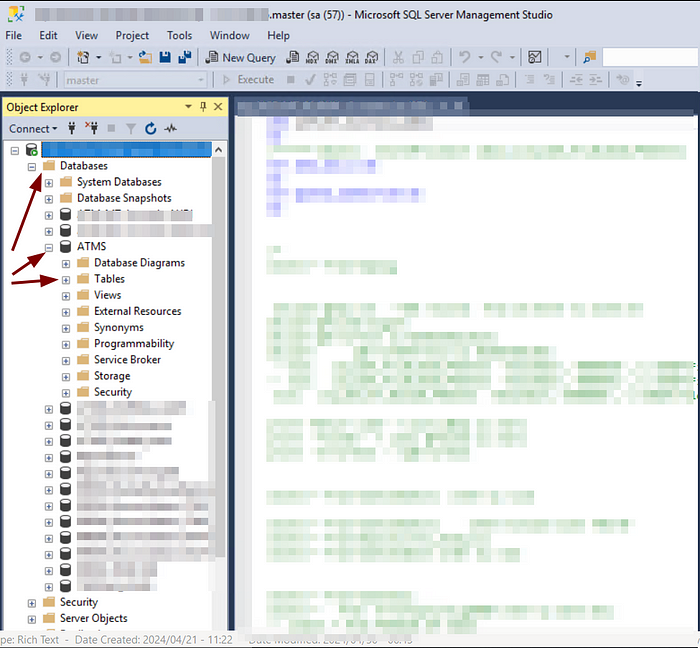
Let’s dump some tables as PoC.


Until now, we have done well, but is this the end?
Of course not. This DBMS is an MSSQL server, so this DBMS has some juicy procedures. like xp_cmdshell, this procedure allows the user to execute commands on the OS, like cmd.
So let’s check if this procedure is enabled or not. (Be noted: this procedure is disabled by default, and to enable it, you must have a SA account.)
I will use this query to check the availability of this function.
SELECT * FROM sys.configurations WHERE name = 'xp_cmdshell'I found it enabled, as shown in the image below.

Let’s try to execute simple commands.
exec master..xp_cmdshell 'powershell -c whoami'
exec master..xp_cmdshell 'powershell -c whoami /priv'

And finally, get a reverse shell.

I tried to get NT AUTHORITY\SYSTEM from the service account using the JuicyPotato exploit,but I couldn’t
And that’s it
وفي الاخر حابب اقول سُبۡحَٰنَكَ لَا عِلۡمَ لَنَآ إِلَّا مَا عَلَّمۡتَنَآۖ إِنَّكَ أَنتَ ٱلۡعَلِيمُ ٱلۡحَكِيمُ









